
Actively exploited vulnerability gives extraordinary control over server fleets
On Wednesday, CISA added CVE-2024-54085 to its list of vulnerabilities
Read more
On Wednesday, CISA added CVE-2024-54085 to its list of vulnerabilities
Read more
Can you recall the last time you opened a bank
Read more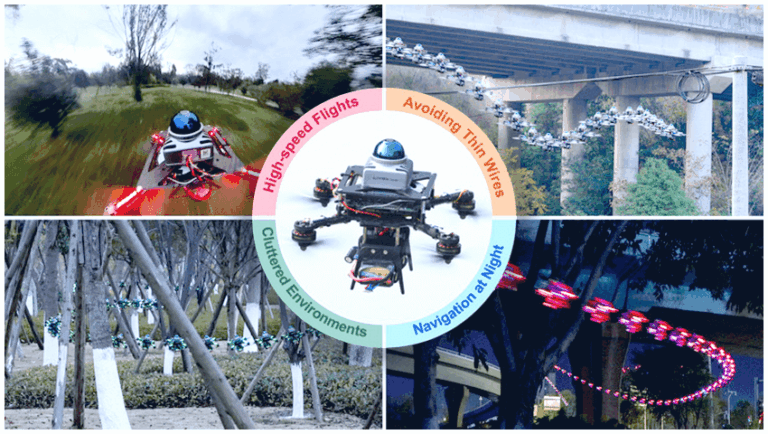
Traditional drone navigation systems rely on pre-mapped environments or slow
Read more
Twitter is one of the majorly popular social media platforms
Read more
RabbitMQ is one of the most popular open-source message brokers
Read more
The widely read and discussed article “AI as Normal Technology”
Read more
Renaming a column in Postgres might seem straightforward, but as
Read more
If you’ve ever watched a student light up after cracking
Read more
Research has shown that large language models (LLMs) tend to
Read more
Enjoy Barista-style coffee in the comfort of your own home,
Read more